Office security guide
What is office security?
Office security is about keeping your workplace safe — not just the building, but also the people, equipment, and information inside. It covers three main areas:
- Physical security: Think door locks, cameras, alarms, and visitor management security systems that help make sure only the right people can enter the office.
- Cybersecurity: Protecting your digital information — like emails, files, and systems — from hackers or data leaks.
- Employee security: Having simple rules for how to report problems, handle sensitive info, and respond to workplace security issues. It also means teaching employees what to look out for, encouraging everyone to speak up if something feels off, and protecting those who report concerns.
When all of these work together, your workplace is safer, more secure, and better prepared for anything that might come up.
Why is office security important?
Office security is important because it:
- Keeps people safe. Office security protects your team, visitors, and anyone in the building from danger or harm.
- Makes sure only the right people get in. Security systems help control who can enter certain rooms or use certain files, so people only go where they’re supposed to.
- Keeps important information safe. Workplace security also protects your passwords, client details, and company documents from being stolen or leaked.
- Helps during emergencies. If there’s a fire or other emergency, it’s important to know who’s in the building. Good security helps make sure everyone gets out quickly and safely.
- Keeps your company compliant. Many businesses have to meet local safety and security laws. Having strong workplace security helps you follow those rules and avoid problems.
💡 For more insights, check out the latest office security statistics →
What are some workplace security examples?
When you think about keeping your office secure, your mind probably goes straight to security guards and loud alarms. And that makes total sense. But there are quite a few workplace security tools that you should be implementing (and integrating with one another!):
Alarms and sensors
Alarms and sensors help keep your office safe by warning you when something’s not right.
Alarms are loud on purpose — they grab attention fast and can scare off anyone who shouldn’t be there. Sensors can also quietly send alerts to your phone or your team, so you can act quickly.
You can use different types of sensors around the office. For examke, motion sensors can detect movement where no one should be, door sensors can tell if a door is forced open, and smoke detectors can warn you about fires.
Security cameras
Security cameras help you see what’s happening in and around your office. They’re great for watching over your office in real time, but they’re also incredibly helpful when you need to go back and check what happened after an incident, like if something went missing or someone entered a space they weren’t supposed to.
Today’s camera systems are smarter than ever, especially when they work together with your access control and visitor management software.
💡 For example, when someone unlocks a door, the nearby camera can start recording automatically. That way, you don’t just know that a door was opened — you can actually see who opened it and when. Everything is time-stamped and linked, which makes it easy to piece things together later.
Access control system
Access control is all about managing who can enter different areas in your office. Instead of using regular keys, you can use keycards, phone apps, or fingerprint scanners. These systems make sure that only the right people can open certain doors, and they also keep track of who went where and when.
💡 For example, maybe only your IT team should go into the server room. With an access control system, you can set that up easily. And if something strange happens, like a door being opened after hours, you can quickly check the system to see who was there.
Modern access control tools like Kisi or Tapkey make managing door access really easy, especially in offices with flexible schedules or multiple locations. You don’t always need someone at the front desk to let people in. Employees can use one secure ID (like a phone or badge) to get into the areas they’re allowed in, and even use the same ID for lockers and printers.

To make it even smoother, you can connect your access control system to a Single Sign-On (SSO) service. This means employees only need one set of login details for everything, from opening doors to signing into work tools. It makes things simpler for your team and adds another layer of security too.
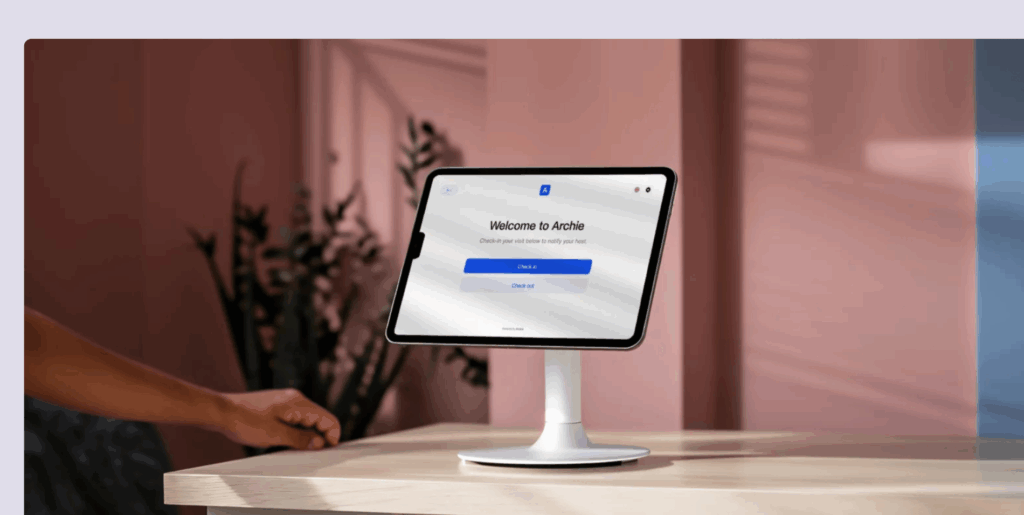
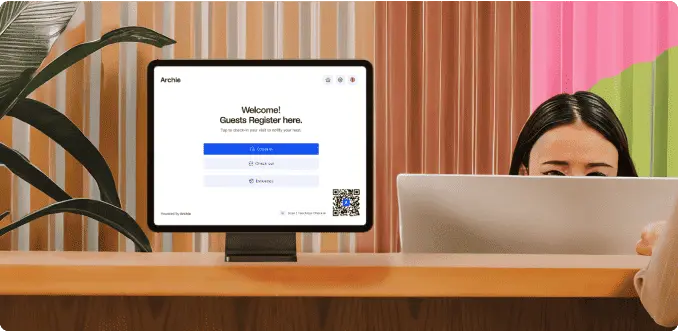
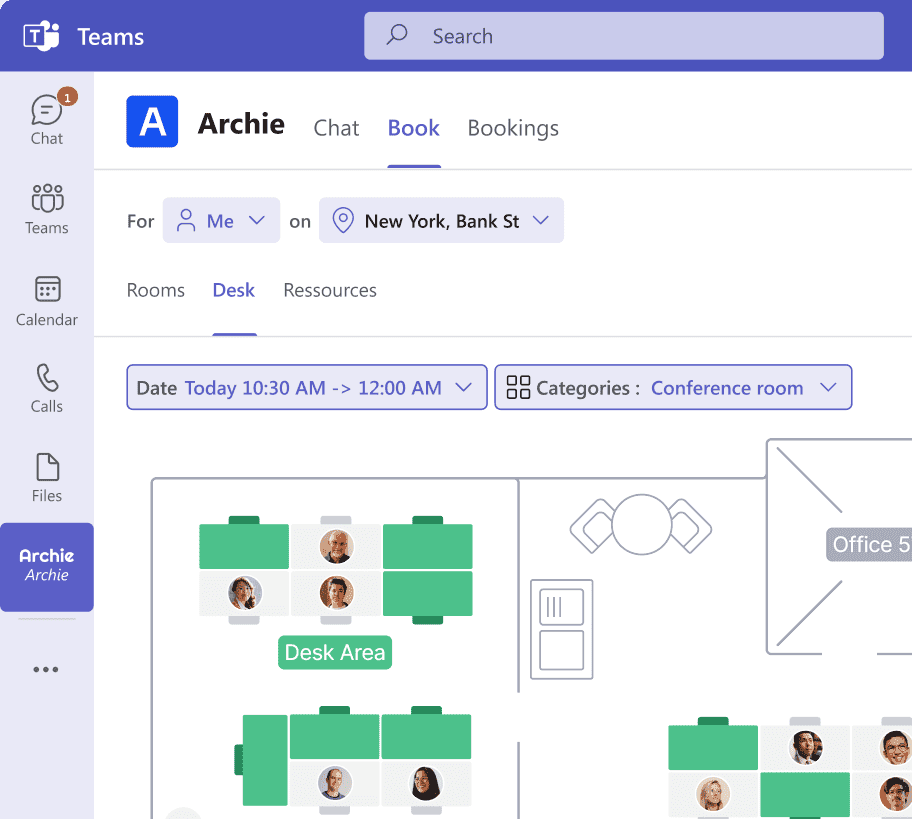
Visitor management security system
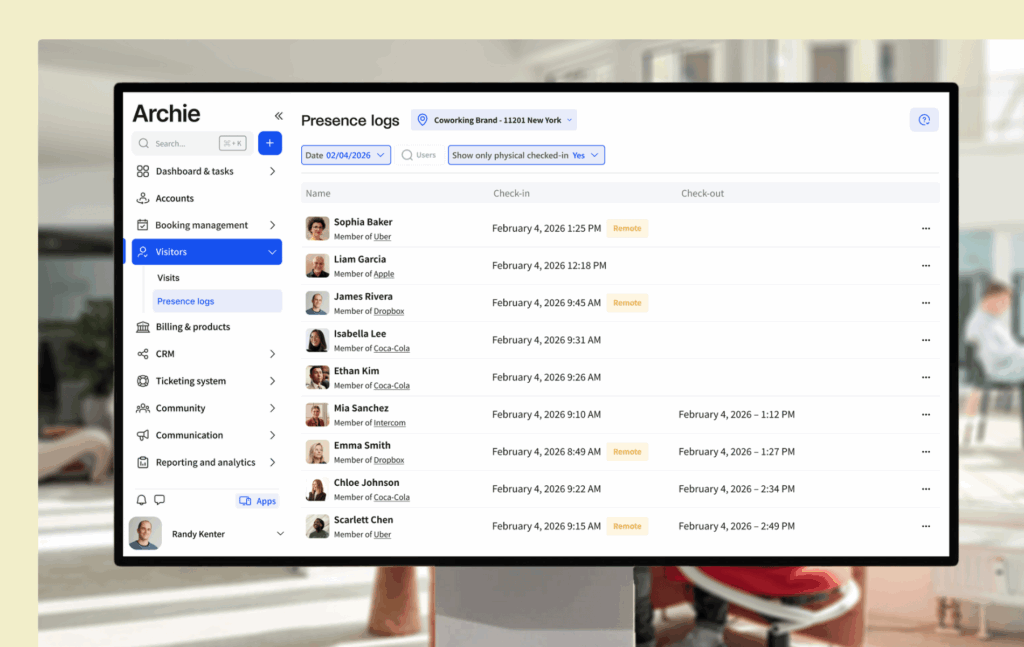
Visitor management systems like Archie help you keep track of who’s coming in, why they’re there, and who they’re meeting. While it might seem like a small thing, they play a big role in your overall security setup, and work best when connected with door access systems and security cameras.
Here’s how it usually works: when a visitor arrives, they check in at the front desk or on a tablet. The system records their name, photo, reason for visit, and who they’re there to see. They get a visitor badge so everyone knows they’re not an employee, and the system logs the time they arrived. This may sound simple, but it’s really useful if something goes wrong.
💡 For example, if your office has a rule that visitors must wear badges, it’s easier to notice if someone tries to sneak in without checking in (this is called tailgating). Your PoE cameras might catch it, and the visitor system helps confirm who was supposed to be there, and who wasn’t.
Or maybe a visitor who signed in goes into a space they’re not allowed in. If you’re using a system like Archie, you can quickly check their details — like when they arrived, who they were visiting, and even see their photo. You can match that with video footage and door access logs to understand exactly what happened, even if it was weeks ago.
Passwords and online protection tools
Office security isn’t just about locked doors and cameras, it also includes protecting your emails, files, and systems with strong passwords and smart tools.
Tools like Okta or Psono help manage shared company accounts by keeping passwords secure and only letting the right people in. They also help enforce strong password rules across your whole team.
💡 For example, a strong password should use a mix of letters, numbers, and symbols, and avoid easy guesses like “1234” or “password.” Encourage your team to update passwords often and not reuse the same one everywhere. Adding two-factor authentication (2FA), like a code sent to your phone, makes things even safer. Online protection tools are great, but teaching your team how to stay safe online is just as important.
How can you keep your office secure? Best practices
To keep your office safe, consider the following workplace security tips:
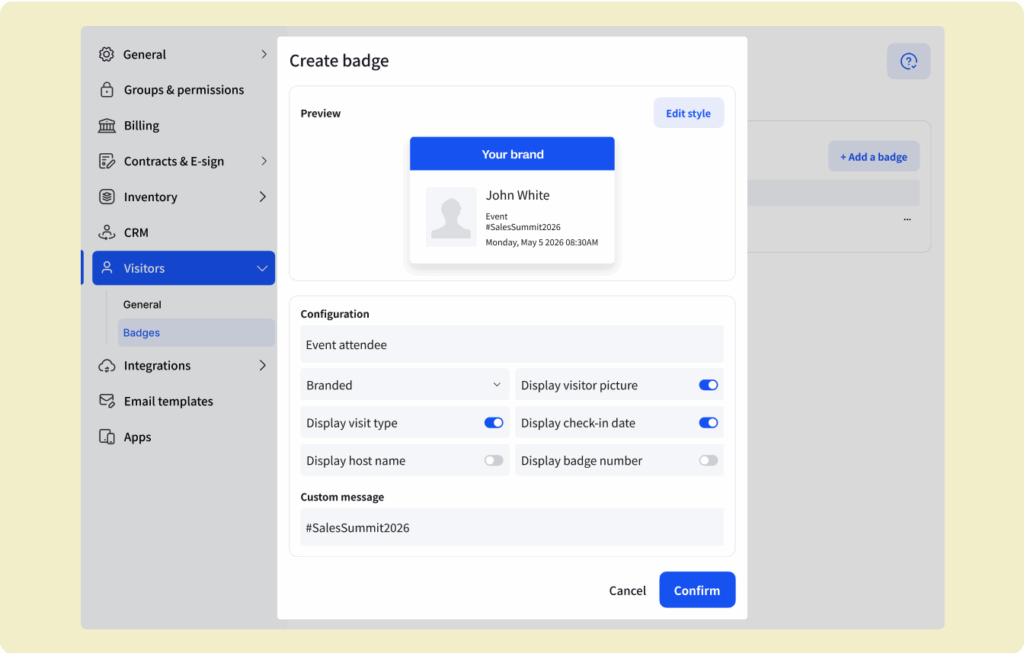
Use badges and access control systems
One of the easiest ways to improve security is by giving employees and visitors badges or digital passes to access certain areas. A badge system makes sure that only the right people can enter specific rooms, floors, or departments. You can set different access levels based on the person’s role — for example, giving IT access to server rooms, but not general employees.
Badges also create digital records of when and where people enter, which can be useful in case of incidents. You can even block access for certain individuals if needed, and connect your system with space management tools to see how the office is being used in real time.
Install cameras and sensors
Security cameras help you monitor what’s happening around the office. Place them at entrances, exits, and other key areas, and if possible, connect them with your access control tools. This way, when a door gets opened, the camera should record it automatically. This makes it easy to match up video footage with entry logs and investigate anything unusual quickly.
Cameras, alarms, and sensors are also great for spotting problems early. Motion sensors can alert you if someone is moving around in a restricted area, while door sensors can detect if a door is forced open. Smoke detectors, of course, are a must for fire safety. Loud alarms can scare off intruders, while silent alerts can notify your security team or send a message to your phone.
Update software regularly
It’s easy to forget, but keeping your workplace tech stack up to date is one of the best ways to stay secure. Updates often fix security issues that hackers might try to use. Encourage employees to keep their devices updated — and consider sending reminders or offering help to those who need it. Speaking of…
Train your team on cyber threats
Your employees are a huge part of your security team. Regular training sessions on topics like phishing, password safety, and internet do’s and don’ts can go a long way. Make these sessions short, friendly, and open for questions. You’ll be surprised how much your team picks up — and how many threats they can help you avoid.
Do regular security checkups
Every now and then, take a step back and assess your security setup. A security audit, either done by your team or a professional, can help you spot gaps and suggest improvements. Things change over time, so reviewing your systems regularly helps you stay ahead of new risks.
Have a visitor policy in place
Visitors should never be able to just walk into your office unannounced. A good visitor policy outlines who can visit, where they can go, and when. You might also require visitors to be escorted during their stay or give advance notice if they need access to sensitive areas. Make sure all employees know these rules and follow them, too!
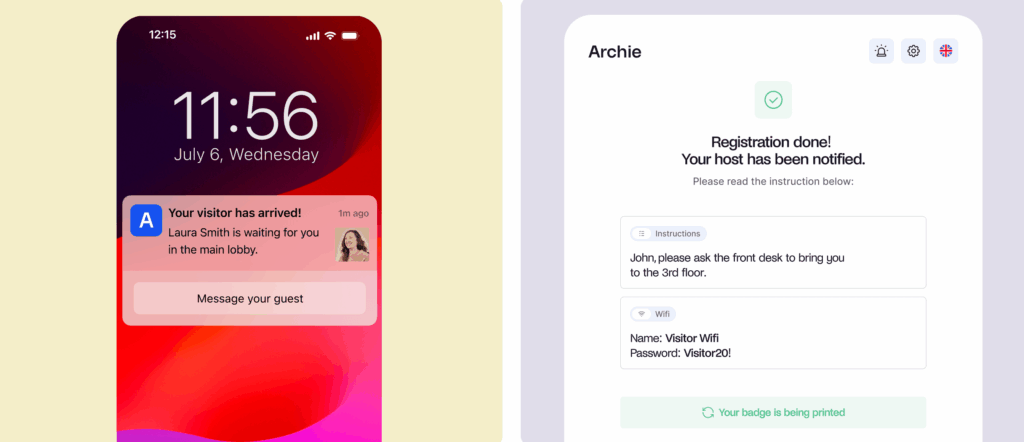
The front desk is your first line of defense. Secure systems like Archie let visitors check in on a tablet, capture their photo, issue a badge, and record who they’re meeting and when, to give you a complete presence log of everyone in the building at all times.
Keep your office secure with Archie
Archie’s visitor management security system lets you manage who enters your space, track who’s onsite, and handle emergencies, all in one place:
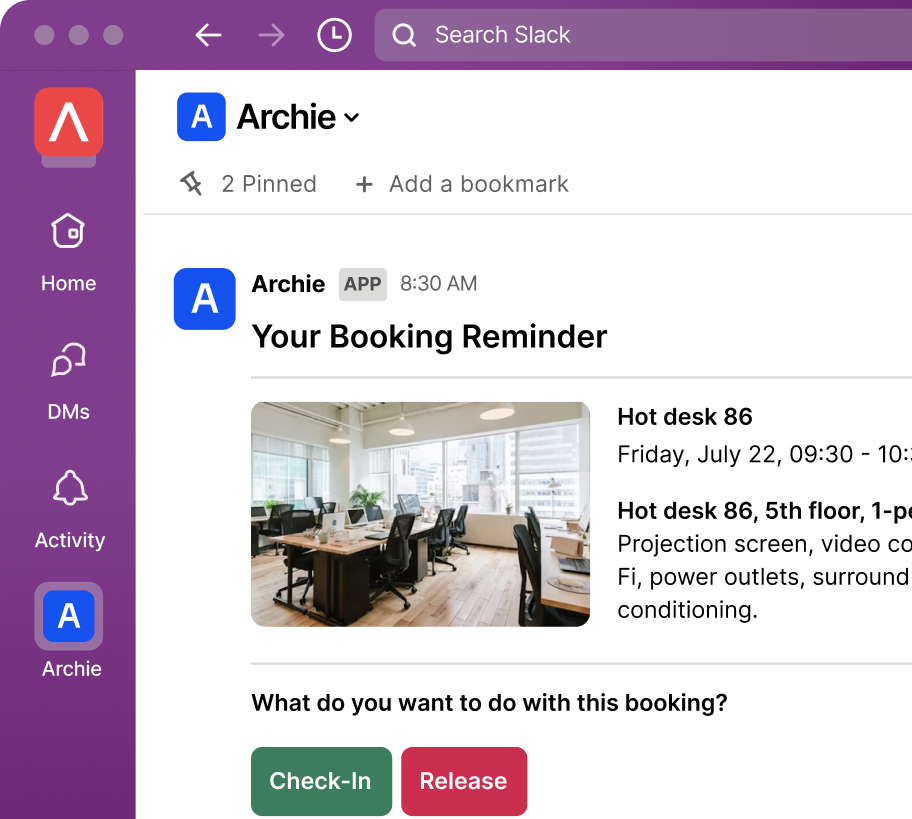
- Know who’s in the office: With Archie, visitors check in quickly using a tablet or kiosk. You can take their photo, print a badge, and collect any documents like NDAs. All visits are logged, so you always know who was in the building and when. You can even safely share WiFi access without giving out the password.
- Handle emergencies with confidence: If there’s ever an emergency, you can send alerts to everyone in the building. People can mark themselves as safe in the app, and you can run quick roll calls to check who’s out. Archie also lets you notify visitors if the office is closed or when it’s safe to return.
- Control door access: Archie works with popular door access systems like Kisi and Tapkey. You can unlock doors from the app, set who can enter where and when, and update permissions automatically — no extra hardware needed.
- Manage deliveries easily: Archie also helps with mail and packages. You can match deliveries to the right person, send them a quick notification, and let them pick up their items safely through a kiosk.

Berenika Teter
Archie's Content Manager, fueled by filter coffee and a love for remote work. When she’s not writing about coworking spaces and hybrid workplaces, you can probably find her exploring one.








![Envoy Software Review: Features, Pricing, Pros & Cons [2026] Office space full of desks.](https://archieapp.co/blog/wp-content/uploads/2025/10/Envoy-software-overview-cover-image-400x400.jpg)