TL;DR: Key statistics shaping modern office security
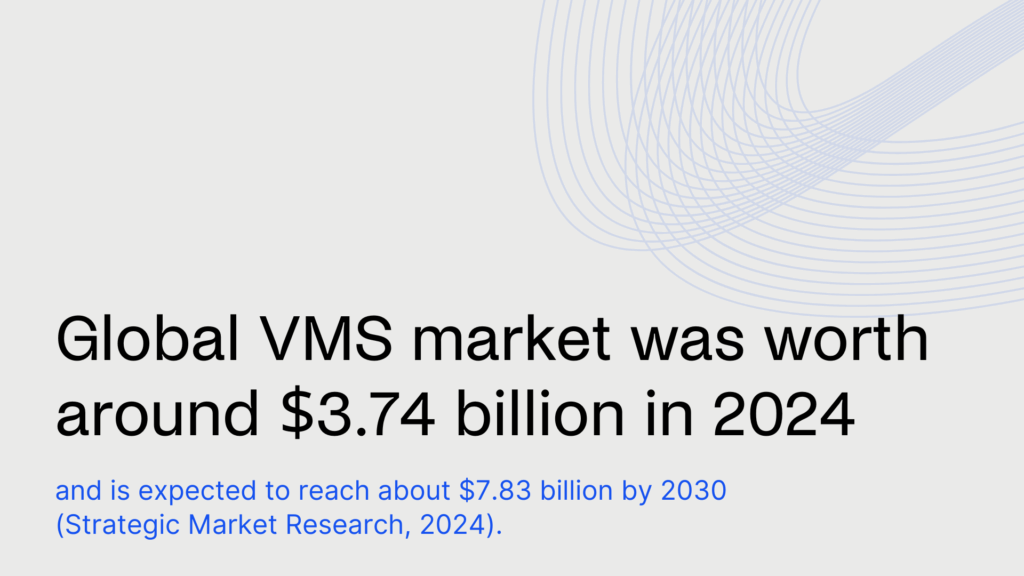
- Global market growth: The visitor management system (VMS) market was worth $3.74 billion in 2024 and is expected to reach $7.83 billion by 2030. (Strategic Market Research, 2025).
- Mobile identity adoption: 61% of security leaders rank mobile identity growth among the top industry trends, and nearly two-thirds have deployed or plan to deploy mobile credentials (HID Global, 2025).
- Continued use of physical badges: 63% of organizations still use physical ID badges, while 39% use mobile IDs and another 39% use biometrics (HID Global, 2024).
- Identity-based intrusions are on the rise: 30% of cyber intrusions used valid accounts, and another 30% came from public-facing app exploits. Phishing-delivered infostealer attacks rose 84% year over year, and ransomware accounted for 28% of malware cases (IBM, 2025).
- SME cyber exposure: 59% of small and mid-sized firms were attacked in the past year, and 27% faced ransomware. Entry points included IoT devices (33%), supply-chain weaknesses (28%), and cloud services (27%) (Hiscox, 2025).
- Security investment trends: 60% of business leaders are increasing cyber-risk budgets and making AI a top priority, but only a small fraction have fully implemented mature data-risk controls (PwC, 2025).
Guide to office security statistics
The state of the visitor management industry
The visitor management industry is growing fast and becoming a major part of how workplaces handle safety, compliance, and day-to-day operations.
According to Strategic Market Research, the global visitor management system (VMS) market was worth around $3.74 billion in 2024 and is expected to reach about $7.83 billion by 2030, showing a strong 12.7% compound annual growth rate (CAGR).
Another report by Mordor Intelligence paints a similar picture. It values the market at $2.13 billion in 2025 and projects it will grow to $4.19 billion by 2030 at an even higher 14.49% CAGR.
The two reports use slightly different baselines and definitions, but both agree on one thing: adoption is rising quickly. Offices, hospitals, schools, and government facilities around the world are investing in modern systems to keep better records of who enters their buildings, strengthen physical security, and meet data-privacy and compliance standards.
The rise of visitor management software
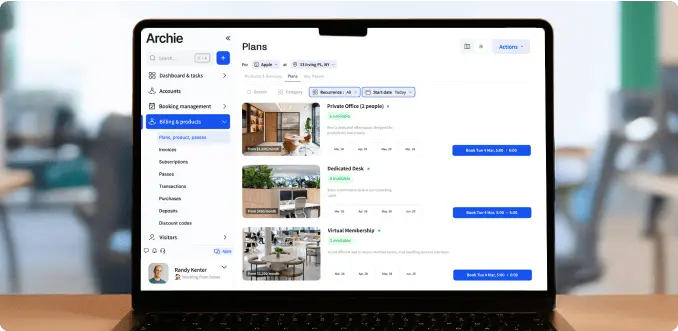
When we look closer at what’s driving that growth, visitor management software takes the lead in market share. Cloud-based systems like Archie now dominate new rollouts because they’re easier to manage, scale, and integrate across multiple locations.
Hardware like visitor kiosks, badge printers, and ID scanners is still important, but most of the value lies in the software layer that connects everything and offers powerful features (think pre-registration, access permissions, analytics, and reporting).

Corporate offices make up the largest share of spending, as companies focus on creating secure yet welcoming entry experiences. At the same time, healthcare and education are catching up quickly due to tighter safety rules and the need for traceable visitor records.
Different sectors, different goals
- Corporate offices use it to project professionalism and streamline guest experiences while meeting compliance requirements. Automated pre-registration, instant host alerts, and badge printing are the most common features.
- Healthcare facilities rely on VMS for infection control, credential verification, and patient safety. Systems often include zone restrictions so visitors can only access approved areas such as wards or labs.
- Schools and universities use visitor tracking to enhance campus safety. Many scan IDs or run background checks against watchlists before granting access.
- Industrial and logistics sites combine visitor management with contractor safety training and credential checks, often linking systems to access gates, turnstiles, or time-tracking tools.
- Government and defense facilities integrate visitor data with national ID databases and access-control systems to verify clearances in real time.
From a regional view, North America continues to lead in overall market size thanks to strict workplace compliance requirements and a mature security ecosystem. Europe follows closely, with strong demand for GDPR-compliant visitor-data handling and auditability. The Asia-Pacific region is growing the fastest, fueled by smart-city investments, large tech campuses, and expanding industrial zones.
All these signs point to a clear trend: visitor management is no longer a nice-to-have front-desk tool. It’s becoming an essential part of workplace security and digital transformation strategies worldwide.
What’s changing in the lobby (and beyond)
The office lobby looks very different today than it did just a few years ago. What used to be a simple check-in desk with paper logs has evolved into a connected digital checkpoint that’s tightly linked with other workplace systems.
According to Strategic Market Research, modern visitor management systems have become full-fledged identity and access hubs. They now integrate directly with tools like access control, security cameras, elevators, calendars, and even HR systems to give companies a complete picture of who’s entering their buildings, where they’re going, and for how long. This deeper integration means visitor data no longer sits in isolation.
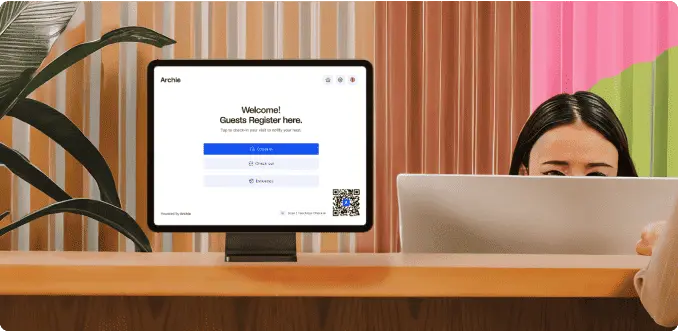
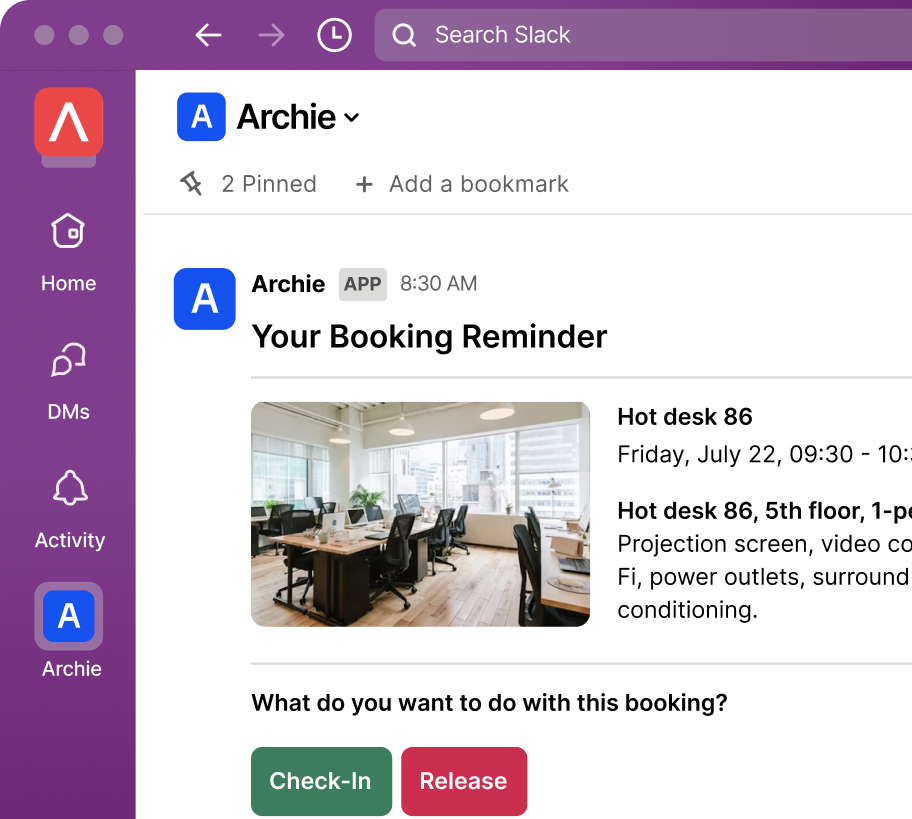
The shift toward touchless check-in experiences is one of the biggest changes. After the pandemic, people expect smooth, hygienic, and contact-free check-ins. QR-code scanning, mobile passes, and facial recognition are now standard options rather than premium add-ons. In high-security environments like labs or data centers, facial-matching technology helps confirm identity without the need for physical badges or manual verification.
Analytics have also moved to the forefront. Modern VMS platforms can track real-time data such as visitor volume, average check-in time, peak hours, and even after-hours activity or repeated visits by the same individuals. Security and facility teams use these insights to spot unusual patterns, like non-compliant visitor behavior or unexpected contractor access, and take action quickly.
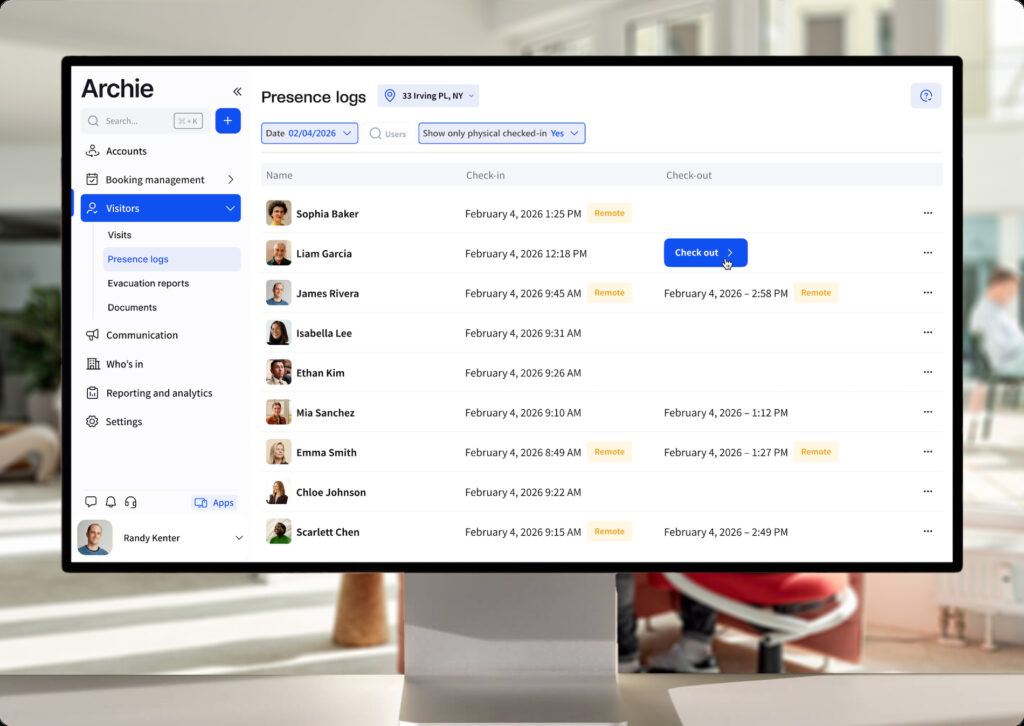
The result is a lobby that works faster, feels more professional, and strengthens accountability. Instead of waiting in line to sign a sheet, visitors receive a digital invite, scan a code on arrival, and their host gets an instant notification. For the organization, this means faster, more secure, and fully auditable entry records, ensuring that at any given moment, it’s clear who’s in the building and why.
Mobile credentials are rising, but…
Mobile credentials are moving from “nice-to-have” to mainstream. In HID’s 2025 industry survey, 61% of security leaders rank the growth of mobile identity among the top trends, and almost two-thirds have either deployed mobile credentials already (37%) or plan to do so (32%).
Most organizations aren’t going all-in on one method, though. 84% still run a hybrid setup (mobile + physical cards), and nearly half (48%) still require a visible ID on the person, which remains especially useful for visitors and contractors.
At the same time, teams are consolidating tools: 67% of security leaders and 73% of integrators/consultants report a shift toward unified, software-driven platforms that tie video, access control, and intrusion together to speed up response and simplify daily work.
Badges stay put (for now)
Ground truth from HID’s 2024 access control study, on the other hand, shows why hybrid is sticking around. Physical badges are still in active use at 63% of organizations, even as mobile IDs (39%) and biometrics (39%) keep growing.
Many sites also keep legacy card tech running — for example, 33% still support 125 kHz prox and 28% still use magstripe, alongside newer encrypted options. Looking ahead, more than half plan upgrades over the next six years, with software (54%), readers/credentials (53%), and controllers (50%) topping the list.
If you’re refreshing your stack, this is the perfect moment to line up visitor flows, badge issuance, and data-retention rules so everything works together.
AI and analytics: from dashboards to anomaly detection
AI has moved from buzzword to “on the roadmap.” In offices, you’ll see it in three practical places: identity checks (e.g., face-match for high-security areas), anomaly spotting (flagging out-of-zone movement or unusual after-hours contractor activity), and faster incident summaries that pull signals from access logs, cameras, and visitor records. Buyers also want open, interoperable platforms so these AI features plug into what they already run today, and whatever they add tomorrow.
HID’s latest research captures this shift, and PwC’s global survey points in the same way from the cyber side. Most organizations use or plan to use AI for threat hunting, event detection/behavior analytics, identity and access management, and vulnerability scanning over the next 12 months. Talent, cost, and integration are common hurdles, so the practical play is to start small with data-rich use cases (like after-hours anomalies or repeated denied entries), measure the lift, then expand.
The threat picture: identity abuse and exposed apps lead
Attackers are getting in the easy way — by logging in. IBM’s 2025 X-Force report shows that about 30% of intrusions used valid accounts, and exploits of public-facing apps were tied for the top entry point at ~30%. Phishing-delivered infostealers jumped 84% year over year, which helps criminals steal credentials and blend in as real users. IBM also notes manufacturing is the most-attacked industry for the fourth year running, and APAC saw the largest share of incidents (34%) with a 13% rise.
Ransomware still matters too, making up 28% of malware cases, even as overall incidents trend down. Taken together, this argues for short-lived guest passes, least-privilege roles, MFA for admins/hosts, and hardening any internet-facing portals (WAF/CDN, patching, SSO).
Smaller and mid-sized companies are taking the biggest hit
Hiscox reports 59% of SMEs were attacked in the past 12 months, and 27% faced ransomware. First entry often comes through the physical-meets-IT layer: IoT devices (33%), supply-chain weaknesses (28%), and cloud services (27%), all highly relevant to kiosks, badge printers, cameras, tablets, and third-party visitor systems on your network.

Most SMEs are responding by stepping up hygiene: 94% plan to increase security spend, 91% run quarterly vulnerability checks, and 88% do quarterly supplier risk reviews. If you manage offices, fold these checks into your visitor/access stack and vendor due diligence.
Budgets, boards, and governance
Security budgets are moving up: PwC’s latest Global Digital Trust Insights shows leaders putting more money into cyber risk and placing AI high on their near-term priority lists. At the same time, only a small share say they’ve fully implemented the data-risk controls they need, which means there’s still a gap between ambition and day-to-day practice.
For most companies, the next step is turning strategy into simple, repeatable routines: clear metrics, regular reviews, and tighter identity and access controls across people, devices, and vendors.
For boards, PwC’s guidance is straightforward: ask for decision-useful reporting and map programs to a recognized framework like NIST CSF 2.0 so progress is easy to follow across quarters. In plain terms, that means a concise scorecard showing incidents by type, time to revoke guest access, watchlist hits, after-hours anomalies, and audit-export readiness. This makes visitor and access controls part of the enterprise risk story, not a side project.
Zooming out, the security market itself is services-heavy. The SIA/ASIS global study reminds us that equipment is only one slice of the pie; a lot of the real work (and spend) sits in deployment, integration, training, and ongoing support. That’s why the most successful VMS projects budget for people and process as much as for kiosks, readers, and licenses: think change management for front-of-house staff, admin playbooks for issuing and revoking badges, and tabletop drills that include Facilities, IT, and Security.
What a “secure” VMS looks like: a practical checklist
✅ Identity & credentials
Keep both mobile IDs and visible badges for now. Most organizations still run a hybrid setup, and many sites continue to require on-person ID, especially for visitors and contractors. Plan a phased switch-off of the weakest legacy cards while you add mobile credentials where they help most (frequent guests, contractors). Back this with short-lived visitor passes, least-privilege roles, and MFA for admins/hosts so stolen passwords aren’t enough to get in.
✅ Cloud posture
Standardize on a cloud VMS with SSO/SCIM and open APIs so it plugs cleanly into access control, HR, calendars, and messaging. Put any public pages behind a WAF/CDN, keep them patched, and make audit exports + data-retention settings easy to pull for reviews. (Cloud already holds the majority share of new VMS deployments and is growing faster than on-prem).
✅ IoT hygiene
Your lobby gear is part of your attack surface. Segment kiosks, printers, readers, and cameras on their own network, patch firmware on a schedule, and include them in quarterly vulnerability scans. Treat vendors as third-party risk: run quarterly supplier reviews and ask for SSO/SCIM, short retention, and exportable logs.
✅ Metrics that matter
Track a short set of numbers every quarter and show them to the board on one page:
- Host response time to visitor arrivals
- Watchlist hits and actions taken
- After-hours anomalies
- Audit-export readiness
How Archie helps you build a secure visitor management process
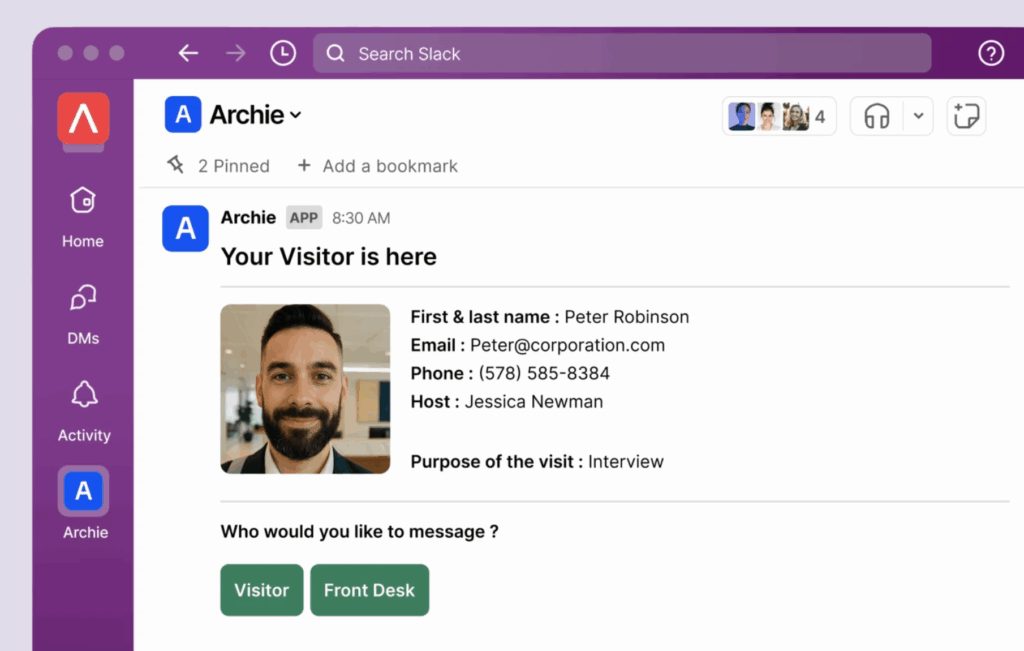
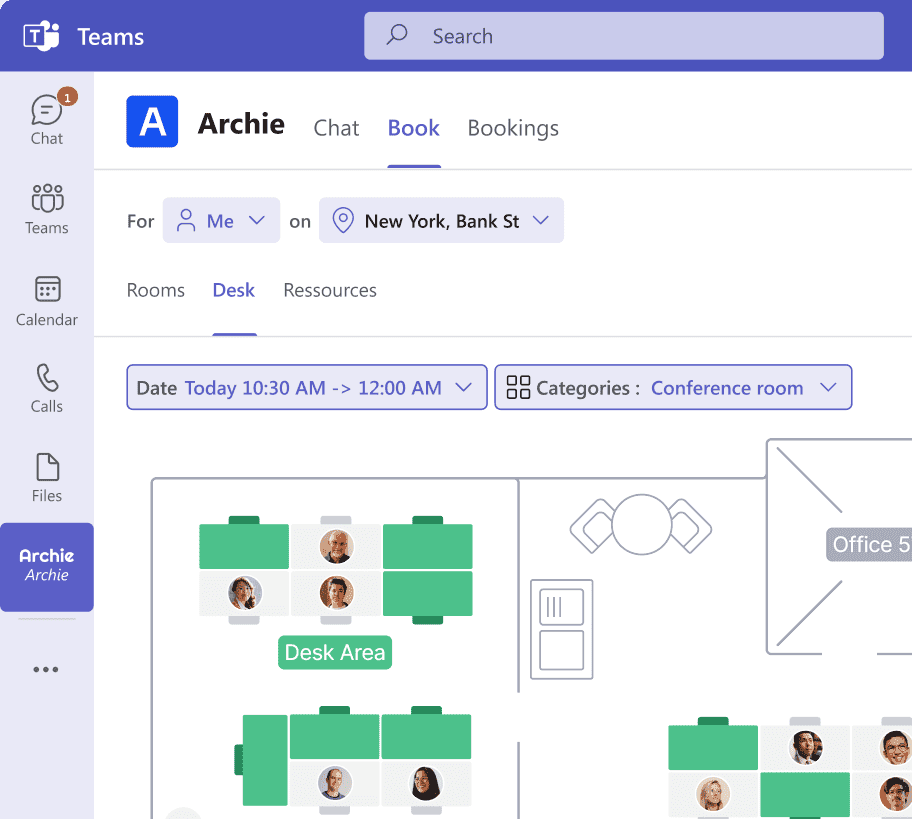
Built for modern workplaces, Archie runs fully in the cloud with enterprise-grade security and uptime. It integrates seamlessly with office tools like Slack, Microsoft Teams, and Outlook, so pre-registration and host notifications are part of your daily workflow.
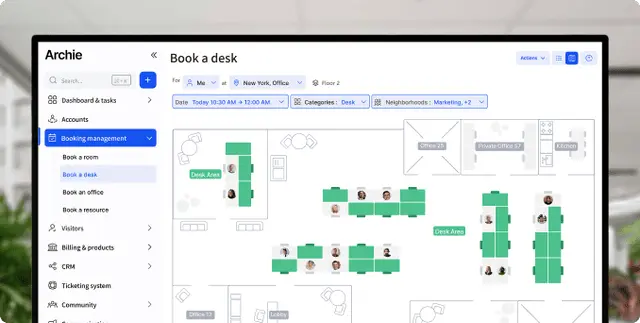
Speaking of workflows, you can set up custom visitor types and flows, issue QR-based mobile passes, and print badges with photos and access labels right at the kiosk. You can also configure time-expiring visitor passes, auto end-of-day sign-outs, and emergency mustering with roll calls and “marked safe” status — helping you know exactly who’s on-site at any moment.

For admins and hosts, Archie supports SSO and SCIM (e.g., Entra ID), ensuring only authorized users manage check-ins. Every visit is logged automatically with timestamps, host details, and digital signatures. See it for yourself.
A summary of the most recent office security statistics
🏢 Market size, segments, and drivers
- The global VMS market was about $3.74 billion in 2024 and is projected to reach $7.83 billion by 2030, which implies a 12.7% CAGR.
- In 2024, software accounted for more than 55% of revenue, while hardware demand is rising as organizations adopt more frictionless check-ins.
- Corporate offices make up the largest application today, with education and healthcare growing quickly.
- Reported operational gains include roughly 60% shorter lobby waits with QR pre-registration, facial recognition accuracy reaching around 99.7–99.9% with fewer false positives, and as much as 85% fewer unauthorized entries at some government sites after real-time ID checks.
- Typical site hardware can reach about $25,000, services often add 30–50% to license fees, and chip shortages have increased hardware costs and lead times.
👤 Access and identity trends
- 61% of security leaders rank mobile identity growth among the top trends.
- About two-thirds have either deployed mobile credentials already (37%) or plan to do so (32%).
- Most organizations still run hybrid identity, with 84% using both mobile and physical credentials.
- Nearly half (48%) still require a visible on-person ID.
- A platform shift is underway, with 67% of security leaders and 73% of integrators reporting a move toward unified, software-driven systems.
- Sustainability now influences purchasing for 75% of organizations.
- Across regions, leaders cite evolving cyber threats, user convenience, and legacy integration as top challenges, with the mix varying by geography.
- Physical badges remain in use at 63% of organizations, while 39% use mobile IDs and 39% use biometrics; 31% use biometrics for two-factor authentication.
- 66% percent tie physical access systems to logical access for computer or network login.
- Many sites still support legacy credentials, including 33% for 125 kHz prox and 28% for magstripe, while newer options such as DESFire (16%) and HID Seos (18%) are growing.
- 41% percent of organizations say they know both the number and location of people on site, while 33% know only the totals.
- The most common tracking method is badge scanning at 48%, followed by time and attendance at 29%, e-rosters at 18%, paper rosters at 17%, and location tracking at 14%.
- Over the next six years, more than half plan upgrades to software (54%), readers and credentials (53%), and controllers (50%).
- Day-to-day priorities include improving user convenience (47%), simplifying PACS administration (41%), protecting against vulnerabilities (38%), integrating with enterprise systems (28%), speeding issue and revoke processes (27%), and knowing who is on site (25%).
- Decision-making is most influenced by physical security teams (71%), IT (53%), facilities (50%), and InfoSec (35%), with procurement and the C-suite also playing roles.
☢️ Threat landscape
- Roughly 30% of intrusions involved the use of valid accounts, and about 30% began with the exploitation of public-facing applications.
- Phishing-delivered infostealers increased by 84% year over year.
- Ransomware still accounted for 28% of malware cases.
- Manufacturing remained the most attacked industry, and APAC saw 34% of incidents, representing a 13% year-over-year increase.
- 59% of SMEs reported a cyberattack in the past 12 months, and 27% reported a ransomware incident.
- The most commonly cited initial entry points were IoT devices at 33%, supply-chain weaknesses at 28%, and cloud services at 27%, with AI tools noted in 15% of cases.
- Among organizations that paid a ransom, 60% recovered some or all data, 41% received a key but still had to rebuild systems, and 31% faced additional payment demands.
- Most organizations plan to increase security spending (94%), conduct quarterly vulnerability checks (91%), and perform quarterly supplier-risk reviews (88%), and 71% report having cyber insurance.
- 65% view AI more as an asset than a risk, while 60% point to AI-driven phishing and social engineering as top emerging threats, and 49% say more decisive leadership would improve incident response.
💵 Budgets, boards, and governance
- 60% of leaders say they are increasing cyber-risk investment.
- Only 6% report fully implementing the key data-risk measures surveyed.
- Over the next year, most plan to use AI for threat hunting, event detection and behavior analytics, identity and access management, and vulnerability scanning.
- Organizations feel least prepared for cloud threats (33%), attacks on connected products (28%), third-party breaches (27%), quantum-related threats (26%), and social engineering (25%).
Sources
- Strategic Market Research, Visitor Management System Market: Segment Revenue Estimation and Forecast, 2024–2030
- Mordor Intelligence, Visitor Management System Market Analysis, Size, Share, and Trends (2025–2030)
- HID Global, 2025 State of Security and Identity: Industry Report
- HID Global, 2024 State of Physical Access: Trend Report
- PwC, Global Digital Trust Insights 2026
- PwC, The board’s role in overseeing cybersecurity (2025–2026)
- IBM Institute, X-Force Threat Intelligence Index 2025
- Hiscox, Cyber Readiness Report 2025
- Security Industry Association (SIA) and ASIS International, Complexities in the Global Security Market: 2024–2026

Berenika Teter
Archie's Content Manager, fueled by filter coffee and a love for remote work. When she’s not writing about coworking spaces and hybrid workplaces, you can probably find her exploring one.








![The Latest Coworking Statistics & Industry Trends [2026] A cozy coworking space with wooden walls, warm lighting, and a large map of South America.](https://archieapp.co/blog/wp-content/uploads/2025/08/Latest-coworking-statistics-cover-image-400x400.jpg)
![RTO: Return-To-Office Statistics, Research & Trends [2026] Modern meeting room with large windows, a wooden conference table, pink chairs, and industrial-style ceiling lighting.](https://archieapp.co/blog/wp-content/uploads/2025/04/RTO-statistics-cover-image-400x400.png)
